AWS Security Groups: A Comprehensive Guide
AWS Security Groups: Controlling Traffic to Your Resources
What is a security group?
An AWS security group functions as a digital barrier, managing the flow of incoming and outgoing traffic to and from EC2 instances. It establishes a series of regulations that determine the types of network traffic permitted to access the instances.
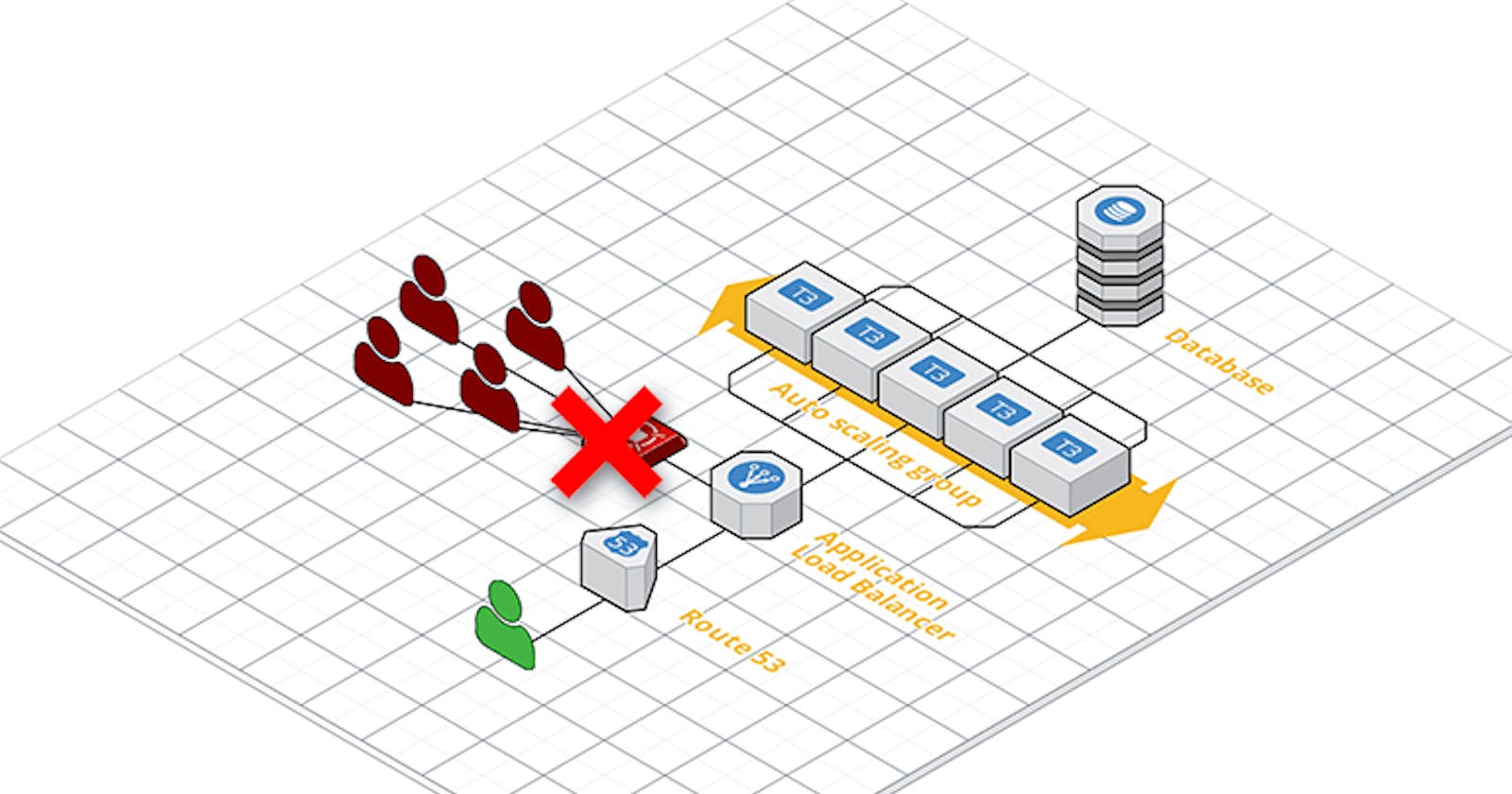
Need and Use Case of Securoty Group
Security groups are essential for securing your EC2 instances by:
Restricting unauthorized access: One can establish regulations to permit solely designated traffic (for instance, SSH access from your IP address) while prohibiting any other unauthorized attempts.
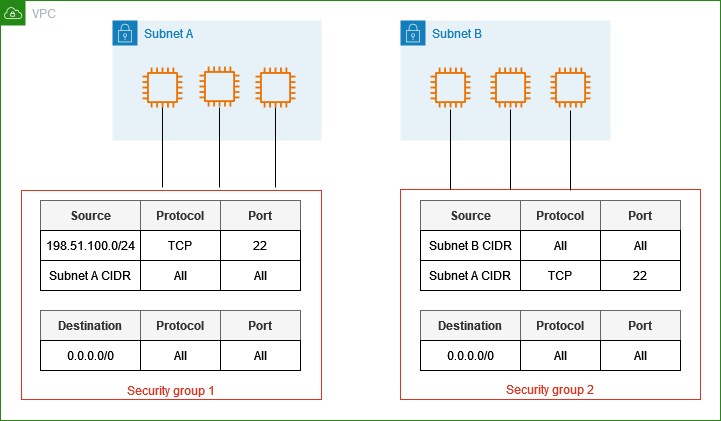
Segmenting your network: Different security groups can be created for various sets of instances, enabling control over their communication with each other as well as the internet.
Complying with security regulations: Security groups play a crucial role in ensuring that security compliance standards are met by limiting access to confidential information.
Adding and Deleting Security Groups to Running Instances
Changes to security groups can be implemented instantly when adding or removing them from running instances. It is possible to assign multiple security groups to a single instance, and conversely, multiple instances can be linked to a single security group.
Multiple Security Groups to One Instance: It is possible to link a maximum of five security groups to one EC2 instance. This feature enables users to merge various security regulations for enhanced and detailed management.
Multiple Instances to One Security Group: It is allowed to attach the same security group to multiple EC2 instances. This simplifies management when the instances have similar access requirements.
Inbound vs. Outbound Traffic
Inbound Traffic: Instances in your Virtual Private Cloud (VPC) may encounter external traffic that seeks to establish a connection with them. This type of traffic, known as inbound traffic, originates from sources outside your VPC. To regulate and manage this incoming traffic, security group rules come into play. These rules determine which specific types of inbound traffic are permitted, such as SSH (Secure Shell) or HTTP (Hypertext Transfer Protocol). By configuring the security group rules effectively, you can ensure that only authorized and necessary inbound traffic is allowed to reach your instances within the VPC.

Outbound traffic: Instances in your network can generate traffic that is intended to reach resources outside of your Virtual Private Cloud (VPC), such as the internet or other VPCs. This type of traffic is referred to as outbound traffic. It is important to note that security groups, by default, do not regulate or control outbound traffic.
Security Rules
Security rules are the individual settings within the security groups that dictate traffic permissions.
They specify protocols, ports, and IP ranges allowed or denied for inbound or outbound traffic.
A security rule defines a specific allowance or denial of traffic based on various criteria:
Protocol: Specifies the type of communication (e.g., TCP, UDP, ICMP).
Port range: Defines the ports on which the traffic is allowed or denied.
Source: Specifies the IP address or security group of the source of the traffic.
Need: Security rules define granular traffic control, ensuring only authorized communication.
Use Case: They are vital for specifying which types of traffic are permitted or denied based on specific requirements.
Types of Security Groups and Rules
Free Tier: Free tier accounts have the same functionalities as paid accounts for creating and managing security groups and rules.
Paid: Paid accounts offer additional features like:
VPC Flow Logs: Record network traffic information for further analysis.
Network Access Control Lists (ACLs): Provide additional control over traffic flow at the subnet level.
Denying Security Rules
While it is not possible to directly establish "deny all" rules, security groups operate on the basis of implicit deny. By default, any traffic that is not expressly permitted by a rule will be restricted. A comparable outcome can be attained by configuring precise allow rules for the intended traffic while leaving all other traffic implicitly denied.
Note:
AWS primarily follows a default deny policy, allowing only explicitly permitted traffic.
While it's possible to configure security groups to deny
Creating Security Groups and Rules
You can create security groups and rules using various methods, including:
AWS Management Console: This is a user-friendly web interface for managing your AWS resources.
AWS CLI (Command Line Interface): Offers a powerful command-line tool for managing AWS resources through scripts.
SDKs (Software Development Kits): Provide programmatic access to AWS services from various programming languages.
Creating Security Group and Rule in an EC2 Instance
Although it is not possible to create a security group or rule directly within a running EC2 instance, they can still be managed through the methods outlined earlier. The following is a basic procedure using the Management Console.
Go to the Amazon EC2 service in the Management Console.
Select "Security Groups" from the navigation pane.
Click on "Create Security Group."
Enter a name and description for the security group.
Click on "Add Rule" to define inbound and outbound rules as needed.
Specify the protocol, port range, source, and action (allow or deny) for each rule.
Review and create the security group.
Once created, go back to your EC2 instance and edit its security group configuration to attach the newly created security group.